I used infographics to update a multimedia object that I had previously created on cybersecurity. I used many of the theories, principles, and skills that I had been taught in the course, EDCI 337. The main idea was to make the multimedia object more effective in knowledge transfer.
Earlier Multimedia
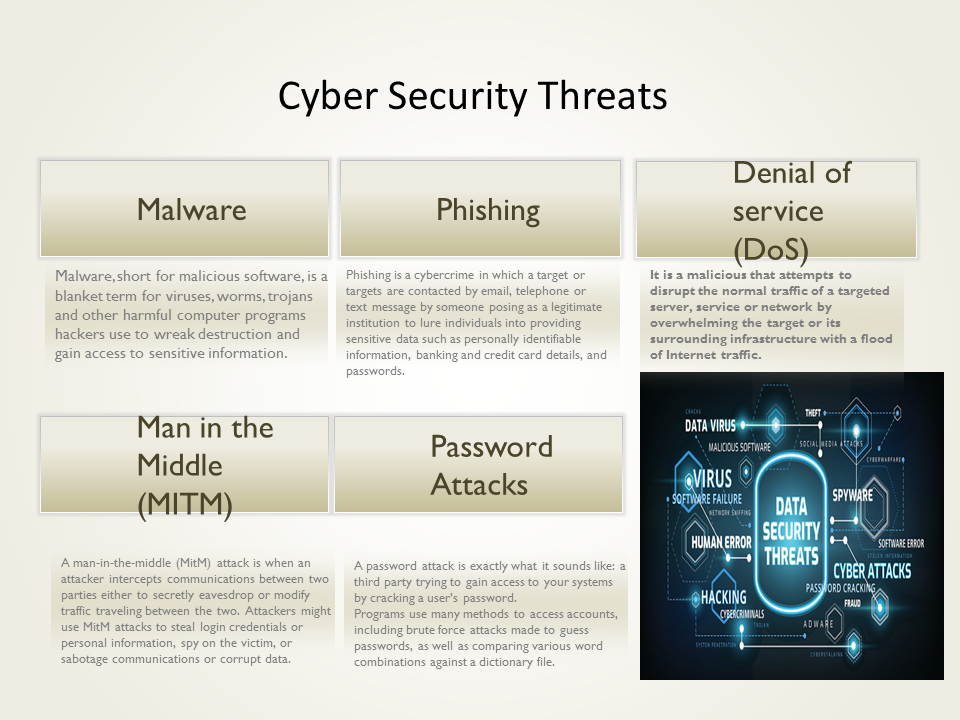
In the earlier infographic, I had not learnt multimedia principles. Therefore, most of the work was self-taught. The infographics had much extraneous material, lacked coherence, and there was no spatial spacing.
Augmentation
I augmented the infographics by using several multimedia principles (Debell, 2020).
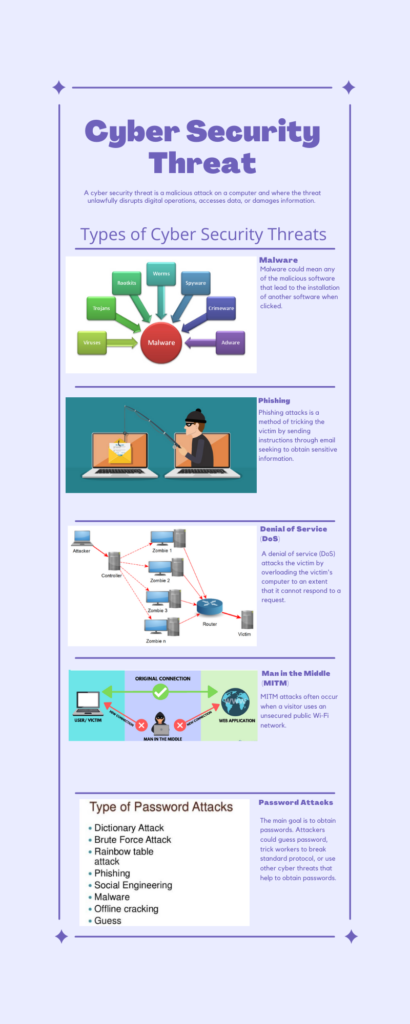
- Coherence – I removed irrelevant texts and pictures. In a bid to avoid cognitive overload, I created summarized texts in most of the information while representing the other information in form of illustrations or pictures.
- Spatial contiguity principle – The new post has proper separations between different cyber security threats. Each threat is then grouped together with a small summary of text form explaining it.
- Redundancy principle – The pictures and texts avoid repetitions. Repetitions increase the cognitive overload by making the learner to read the same information twice.
Skills
I also used various skills and apps that I learned in the course:
- Canva – As taught in the course, I registered for Canva and used it to augment the infographic. Canva is an app that could be used in making brochures, infographics, and posters.
- Use of SAMR Model – SAMR stands for substitution, augmentation, modification, and redefinition. A beginner will move from the enhancing the multimedia through substitution or augmentation to transforming the multimedia through modification and redefinition. The multimedia I used only augmentation.
- Use of SECTIONS Model – SECTIONS is an acronym for students, ease of use, cost, teaching, interaction, organizational issues, networking, and security. The infographic multimedia that I used checks off several boxes, such as students, ease of use, and cost.
Before
After
References
DeBell, A. (2020). How to use Mayer’s 12 principles of multimedia [Examples Included]. Water bear learning. https://waterbearlearning.com/mayers-principles-multimedia-learning/
University of North Dakota. (2021). 7 Types of Cyber Security Threats. https://onlinedegrees.und.edu/blog/types-of-cyber-security-threats/